“Mining wallets with cryptocurrencies is becoming more common as people seek to profit from digital assets, but the reliability and security of this practice are still under scrutiny. Can we truly trust it?”
What is wallet mining?
Wallet mining is the process of attempting to find the private keys to cryptocurrency wallets by systematically guessing or mining these keys using computational power. This involves trying numerous combinations to unlock a wallet and gain control of its funds.
One reason people engage in wallet mining is due to the large number of cryptocurrency wallets that remain unused for a long time. These dormant wallets might be considered lost, as their owners could have forgotten their keys or passed away, leaving the funds inaccessible. By attempting to recover these dormant wallets, some individuals hope to reclaim potentially valuable assets.
Another reason for wallet mining is security. In cases of crime, authorities sometimes use this method to analyze transactions of suspicious wallets. By uncovering private keys, they can track illicit activities and gather evidence against criminals involved in illegal cryptocurrency transactions.
Lastly, hacking is a significant motive behind wallet mining. Many hackers use this method to steal assets by exploiting vulnerabilities in weak or poorly secured private keys. By gaining unauthorized access to wallets, they can transfer funds to their accounts, resulting in substantial financial losses for the original wallet owners.
Wallets and Chains
Each cryptocurrency wallet is connected to a specific blockchain, which is essentially a decentralized digital ledger that records all transactions made with that particular cryptocurrency. A blockchain is unique to its cryptocurrency; for example, Bitcoin operates on the Bitcoin blockchain, while Ethereum operates on the Ethereum blockchain. This means that a wallet created for Bitcoin can only hold and transact Bitcoin, and similarly, an Ethereum wallet can only manage Ethereum and tokens that comply with its standards, such as ERC-20 tokens.
The connection of a wallet to its respective blockchain is crucial for the wallet’s functionality. When a user initiates a transaction, the wallet communicates with the blockchain to verify and record the transaction. This involves broadcasting the transaction to the network, where it is validated by nodes (computers participating in the network) and then added to a block, which is eventually appended to the chain. Each blockchain uses its specific protocols and security measures to ensure the integrity and immutability of the transaction history.

When engaging in wallet mining, knowing which blockchain a wallet is associated with is critical. This is because the process of guessing private keys and validating access attempts must be compatible with the underlying blockchain’s protocols. Each blockchain has unique characteristics, such as address formats, transaction structures, and consensus mechanisms, which influence how wallet mining tools and techniques are applied. For instance, mining a Bitcoin wallet requires different methods and tools than mining an Ethereum wallet, given their distinct cryptographic algorithms and network protocols. Thus, identifying the specific blockchain associated with a target wallet is a fundamental step in the wallet mining process.
Best wallets for each chain:
The wallets discussed here are personal wallets, meaning they are controlled and managed by individual users rather than cryptocurrency exchanges like Binance. Personal wallets provide the owner with full control over their private keys and funds.
Bitcoin:
Ethereum:
Solana:
Dormant wallets:
A dormant wallet is a cryptocurrency wallet that has not had any activity for an extended period. This inactivity means there have been no transactions such as sending or receiving funds, which can occur for various reasons.
These dormant wallets can often be listed on exchanges or websites, with Bitcoin wallets being among the most commonly found due to the cryptocurrency’s widespread adoption and longer history in the market.
“If this information is not readily available on the websites, the date of the last transaction associated with a wallet address can typically be verified through blockchain explorers or cryptocurrency analytics platforms. These tools allow users to inspect transaction histories and details for any given wallet address, providing transparency and accountability within the decentralized network.”
Bitcoin:
Ethereum:
Solana:
Wallet Miners
Wallet mining involves the use of specialized programs or scripts that attempt to generate and test private keys (also known as keys) to gain unauthorized access to cryptocurrency wallets on a blockchain network. These programs are typically developed in programming languages like Python or C++. They function by connecting to the blockchain network where the target wallet is located and systematically generating potential private keys.
In the process, these programs generate cryptographic keys that serve as potential matches for the private key associated with the target wallet. This technique is akin to a digital lock-picking process, where the program continuously injects these generated keys into the blockchain to see if any match the private key of the target wallet. If a match is found, the program gains access to the wallet and can potentially transfer or steal its contents.
“Python-based wallet mining applications exist but are generally considered less efficient due to their slower processing speeds and heavier resource consumption. On the other hand, programs developed in C++ are preferred for their speed and efficiency.”
Paid applications
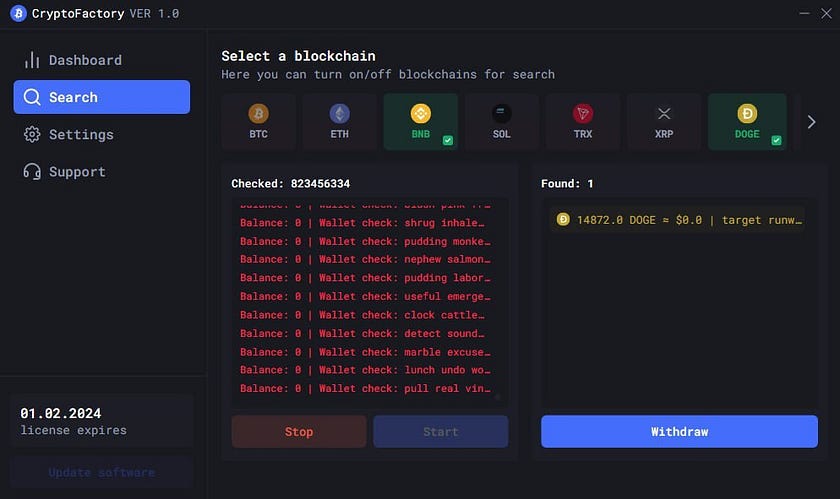
This app provides an interface with nine available chains: ETH, BTC, BNB, SOL, TRX, XRP, DOGE, LTC, and TON, with a base price of $400.
AI Seed Phrase Finder & BTC balance checker tool for Windows PC
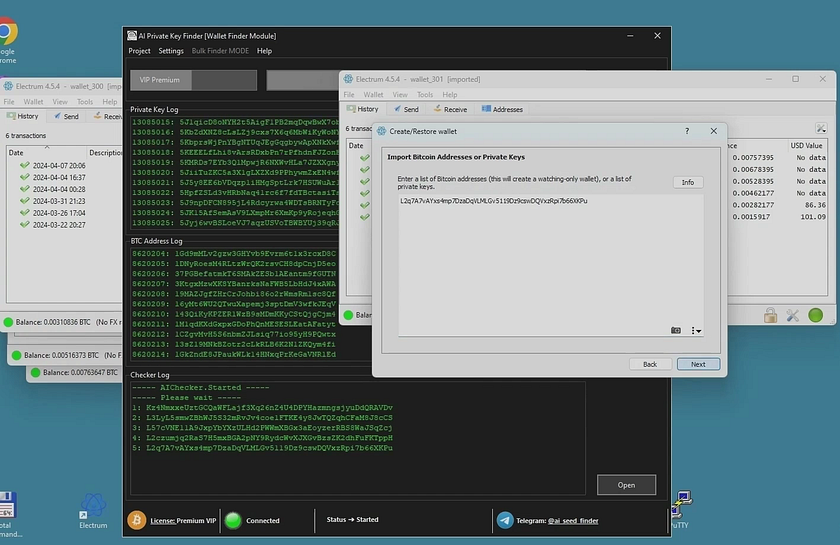
One of the key aspects that sets AI Private Key Finder apart from other similar tools is its use of a remote supercomputer to perform its operations. This unique feature leverages the immense processing power of a supercomputer to execute the complex calculations required to identify private keys. The program exclusively finds key codes for Bitcoin wallets, and users must check the value of the wallets separately.
Written in Python

The codes created in Python can be found on Replit. However, as discussed earlier, they are not recommended.
Written in C++
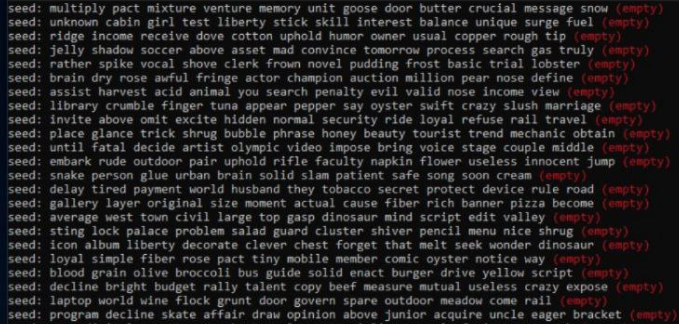
Programs written in C++ are designed to create a unique set of words, known as a seed phrase, which can be used to initialize a cryptocurrency wallet. These seed phrases typically consist of a sequence of 12 randomly generated words.
They support the generation and searching of seed phrases for wallets containing BTC, ETH, LTC, and DOGE coins. The program employs multiple threads to check multiple addresses simultaneously, ensuring fast and efficient searches. All of these programs are available on GitHub.
Disclaimer: These programs have not been back-tested. The use of these programs is entirely at your own risk. Utilizing these programs to access wallets that do not belong to you may constitute illegal and unethical behaviour. The creators of these programs bears no responsibility for your actions or any damage caused to wallets accessed using this softwares. It is strongly advised not to interact with wallets that are found to be currently active without explicit authorization from the rightful owner.
Conclusion
When mining Bitcoin wallets, Electrum is the recommended wallet to check for accessing the funds. For Ethereum wallets, MetaMask is the best option. Always verify the date of the last transaction before assessing minded wallet’s . Additionally, be aware that the wallet you mine could be linked to illicit activities, and any transactions traced to you could have serious legal implications. Remember, unauthorized access to wallets is both illegal and unethical. Overall, I hope this information helps you understand the complexities and responsibilities involved in wallet mining.

Leave a Reply